In today's interconnected world, remote access to IoT devices has become a cornerstone of modern technology. Whether you're managing smart home appliances, industrial machinery, or healthcare equipment, the ability to control and monitor devices from afar is transforming industries. IoT (Internet of Things) devices are no longer just standalone gadgets but integral components of smart ecosystems. As businesses and individuals increasingly adopt IoT solutions, understanding remote access to IoT device examples becomes crucial. These examples not only showcase the potential of IoT technology but also highlight the importance of secure and efficient connectivity. From enabling real-time data analysis to simplifying device management, remote access empowers users to harness the full capabilities of their IoT devices.
However, with great power comes great responsibility. The rise of IoT devices also brings challenges, such as cybersecurity threats, compatibility issues, and user training requirements. That's why exploring remote access to IoT device examples is essential for anyone looking to implement these technologies effectively. By studying real-world applications, you can gain insights into best practices, potential pitfalls, and innovative solutions. Whether you're a tech enthusiast, a business owner, or a developer, understanding how remote access works in IoT environments can help you make informed decisions and optimize your operations.
This comprehensive guide will walk you through everything you need to know about remote access to IoT device examples. From foundational concepts to advanced implementation strategies, we'll cover it all. You'll learn about the benefits, risks, and tools associated with remote access, as well as practical examples to inspire your projects. So, whether you're just starting your IoT journey or looking to expand your knowledge, this article has something for everyone. Let's dive in and explore the fascinating world of IoT remote access together!
Read also:What Is Chip Foose Doing Now A Comprehensive Update On The Legendary Car Designer
Table of Contents
- What Is Remote Access to IoT Device Example?
- Why Is Remote Access to IoT Device Important?
- How Does Remote Access to IoT Device Example Work?
- Can Remote Access to IoT Device Example Enhance Security?
- What Are the Benefits of Remote Access in IoT?
- Top Tools and Platforms for Remote Access to IoT Device
- Challenges and Risks in Remote Access to IoT Device Example
- Real-World Examples of Remote Access to IoT Devices
- Frequently Asked Questions
- Conclusion: The Future of Remote Access in IoT
What Is Remote Access to IoT Device Example?
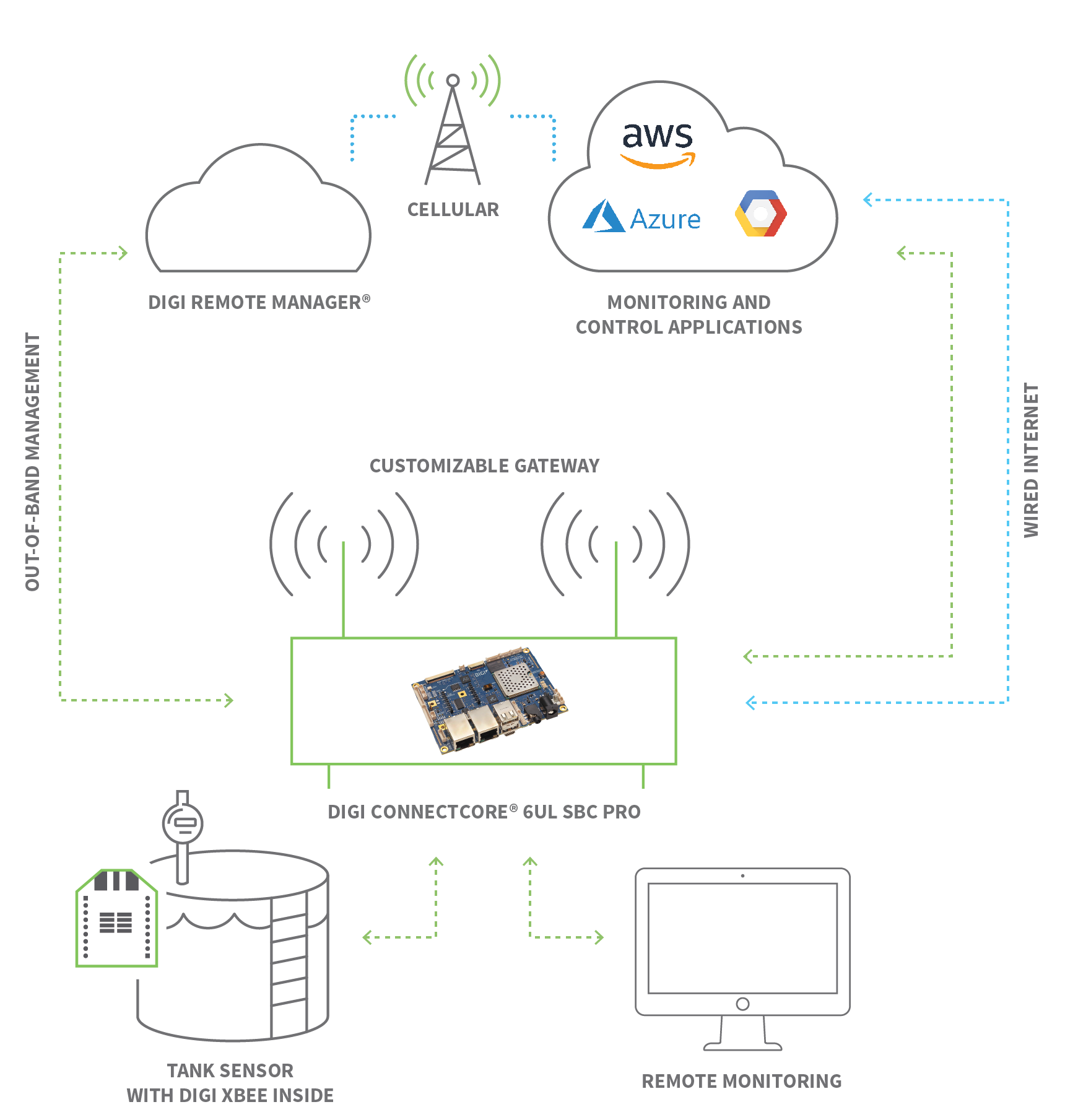
Remote access to IoT device example refers to the process of controlling, monitoring, and interacting with IoT devices from a remote location. These devices, ranging from smart thermostats to industrial sensors, are connected to the internet, allowing users to access them via web-based interfaces, mobile apps, or specialized software. The concept of remote access is not new, but its application in IoT has revolutionized how we interact with technology. For instance, imagine being able to adjust your home's temperature from your office or monitor the performance of a manufacturing plant from another country. These scenarios are made possible through remote access to IoT device examples.
At its core, remote access involves establishing a secure connection between the user and the IoT device. This connection enables two-way communication, allowing users to send commands, receive data, and perform various operations. The architecture typically includes a central server or cloud platform that acts as an intermediary between the user and the device. By leveraging protocols such as MQTT (Message Queuing Telemetry Transport) or HTTP, remote access ensures seamless and reliable communication. Moreover, advancements in encryption and authentication technologies have enhanced the security of remote access systems, making them suitable for sensitive applications.
Why Is Remote Access Essential in IoT?
Remote access is essential in IoT because it addresses several critical needs in modern technology ecosystems. First, it simplifies device management by allowing users to control multiple devices from a single interface. This is particularly beneficial for businesses with large IoT deployments, where manual management would be time-consuming and inefficient. Second, remote access facilitates real-time data analysis, enabling users to make informed decisions based on up-to-date information. For example, a farmer using IoT sensors to monitor soil moisture levels can remotely adjust irrigation systems to optimize crop growth.
Third, remote access enhances flexibility and convenience. Users no longer need to be physically present to interact with their devices, which is especially advantageous in scenarios where distance or travel constraints exist. Lastly, remote access promotes scalability, as it allows IoT systems to grow without requiring significant changes to the underlying infrastructure. By addressing these needs, remote access to IoT device example has become an indispensable tool in the digital age.
How Is Remote Access Implemented in IoT Devices?
The implementation of remote access in IoT devices involves several key steps. First, the device must be equipped with communication capabilities, such as Wi-Fi or cellular connectivity. This ensures that it can connect to the internet and communicate with external systems. Second, a software application or platform must be developed to facilitate user interaction. This application typically includes features such as dashboard visualization, command execution, and data logging. Third, security measures must be implemented to protect the device and its data from unauthorized access. This may involve encryption, multi-factor authentication, and regular firmware updates.
Finally, testing and optimization are critical to ensuring the reliability and performance of the remote access system. By following these steps, developers can create robust and user-friendly solutions that meet the needs of various industries. For example, a healthcare provider might use remote access to IoT devices to monitor patient vital signs in real time, while a logistics company might use it to track the location and status of delivery vehicles.
Read also:23 May Star Sign Unveiling The Zodiac Secrets Of Gemini
Why Is Remote Access to IoT Device Important?
Remote access to IoT devices plays a pivotal role in shaping the future of technology and industry. Its importance lies in its ability to streamline operations, reduce costs, and improve efficiency. By enabling users to manage devices remotely, businesses can minimize downtime, lower maintenance expenses, and enhance productivity. For instance, a manufacturing plant equipped with IoT sensors can detect equipment malfunctions before they occur, allowing for proactive maintenance and preventing costly repairs.
In addition to operational benefits, remote access contributes to environmental sustainability. By optimizing resource usage and reducing energy consumption, IoT devices can help organizations achieve their green goals. For example, smart lighting systems that adjust brightness based on occupancy and daylight levels can significantly reduce electricity usage in commercial buildings. Furthermore, remote access facilitates collaboration and innovation, as teams from different locations can work together to develop and implement IoT solutions.
How Does Remote Access Impact Business Operations?
Remote access has a profound impact on business operations by transforming traditional workflows into digital processes. It allows companies to centralize device management, ensuring consistency and compliance across their IoT deployments. This is particularly important in regulated industries such as healthcare and finance, where data integrity and security are paramount. Moreover, remote access enables businesses to scale their operations without sacrificing quality or performance. For example, a retail chain can use IoT devices to monitor inventory levels across multiple locations, ensuring timely restocking and reducing stockouts.
Another significant advantage of remote access is its ability to enhance customer experience. By providing users with real-time insights and control over IoT devices, businesses can create personalized and engaging interactions. For instance, a smart home provider might offer customers a mobile app that allows them to manage all their connected devices from a single interface. This not only improves convenience but also fosters loyalty and satisfaction.
What Industries Benefit Most from Remote Access to IoT Devices?
Several industries benefit significantly from remote access to IoT devices, including healthcare, manufacturing, agriculture, and transportation. In healthcare, remote access enables doctors and nurses to monitor patients' health conditions in real time, improving diagnostic accuracy and treatment outcomes. In manufacturing, it allows engineers to supervise production lines and identify bottlenecks, leading to increased efficiency and reduced waste. In agriculture, farmers can use IoT sensors to monitor environmental conditions and automate irrigation systems, optimizing crop yield and water usage. Lastly, in transportation, remote access helps fleet managers track vehicles, monitor fuel consumption, and plan routes, enhancing logistics and reducing costs.
How Does Remote Access to IoT Device Example Work?
The functionality of remote access to IoT device example relies on a combination of hardware, software, and network technologies. At the hardware level, IoT devices are equipped with sensors, actuators, and communication modules that enable them to interact with their environment and connect to the internet. At the software level, specialized applications and platforms provide users with the tools they need to manage and control these devices. Finally, at the network level, protocols and infrastructure ensure secure and reliable communication between the device and the user.
For example, consider a smart thermostat that allows users to adjust the temperature of their home remotely. The thermostat contains temperature sensors and a Wi-Fi module that connects it to the internet. A mobile app or web interface enables users to send commands to the thermostat, which are then processed and executed by the device. The entire process is facilitated by a cloud-based platform that manages the communication and ensures data security. By integrating these components, remote access to IoT device example becomes a seamless and intuitive experience.
Can Remote Access to IoT Device Example Enhance Security?
Yes, remote access to IoT device example can enhance security when implemented correctly. Security is a top priority in IoT systems, as these devices often handle sensitive data and perform critical functions. To protect against unauthorized access and cyber threats, developers employ a range of security measures, including encryption, authentication, and access control. For example, encryption ensures that data transmitted between the device and the user is scrambled, making it unreadable to attackers. Authentication verifies the identity of users and devices, preventing unauthorized access. Access control restricts what users can do with the device, limiting potential damage in case of a breach.
Moreover, regular firmware updates and vulnerability assessments help maintain the security of IoT devices over time. By addressing known vulnerabilities and implementing best practices, developers can create robust and secure remote access systems. However, it's important to note that no system is completely immune to attacks. Therefore, users must remain vigilant and follow security guidelines to minimize risks.
What Are the Key Security Features of Remote Access Systems?
The key security features of remote access systems include end-to-end encryption, multi-factor authentication, role-based access control, and secure boot. End-to-end encryption ensures that data is protected during transmission, while multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of verification. Role-based access control restricts access to specific functions based on user roles, reducing the risk of accidental or intentional misuse. Secure boot ensures that the device only runs trusted software, preventing malicious code from being executed. Together, these features form a comprehensive security framework that protects IoT devices and their users.
What Are the Benefits of Remote Access in IoT?
Remote access in IoT offers numerous benefits that make it an attractive solution for businesses and individuals alike. First, it enhances convenience by allowing users to manage devices from anywhere at any time. This is particularly beneficial for busy professionals who need to stay connected to their IoT ecosystems while on the go. Second, remote access improves efficiency by automating routine tasks and providing real-time insights. For example, a smart office building might use IoT devices to automatically adjust lighting and HVAC systems based on occupancy patterns, reducing energy consumption and maintenance costs.
Third, remote access promotes scalability by enabling businesses to expand their IoT deployments without significant investments in infrastructure. This is especially advantageous for startups and small businesses with limited resources. Lastly, remote access fosters innovation by encouraging collaboration and experimentation. By providing users with access to cutting-edge technologies and tools, remote access to IoT device example inspires creativity and drives progress in various fields.
How Does Remote Access Improve Device Management?
Remote access improves device management by centralizing control and simplifying operations. Instead of managing each device individually, users can manage multiple devices from a single interface, reducing complexity and saving time. For example, a facility manager might use a remote access platform to monitor and control all the IoT devices in a building, such as lighting, HVAC, and security systems. This centralized approach not only enhances efficiency but also improves consistency and compliance with organizational policies.
Additionally, remote access enables proactive maintenance by allowing users to detect and address issues before they escalate. For instance, a manufacturing plant might use IoT sensors to monitor the health of its equipment and schedule maintenance tasks based on predictive analytics. By taking a proactive approach, businesses can minimize downtime, reduce repair costs, and extend the lifespan of their equipment.
What Are the Cost Savings Associated with Remote Access?
The cost savings associated with remote access to IoT device example are substantial. By reducing the need for on-site visits, businesses can lower travel expenses and labor costs. For example, a utility company might use remote access to IoT devices to read meters and perform inspections without sending technicians to the field. This not only saves money but also improves response times and customer satisfaction. Furthermore, remote access enables businesses to optimize resource usage and reduce waste, leading to additional cost savings. For instance, a smart irrigation system that adjusts water flow based on real-time weather data can significantly reduce water consumption and associated costs.
Top Tools and Platforms for Remote Access to IoT Device
Several tools and platforms are available for remote access to IoT devices, each offering unique features and capabilities. Some of the most popular options include:
- Microsoft Azure IoT Hub: A cloud-based platform that provides secure and scalable communication between IoT devices and applications.
- Amazon Web Services IoT Core: A managed service that allows users to connect, monitor, and manage IoT devices at scale.
- Google Cloud IoT Core: A platform that enables users to securely connect and manage IoT devices using MQTT and HTTP protocols.
- IBM Watson IoT Platform: A comprehensive solution that combines IoT connectivity with advanced analytics and AI capabilities.
- Particle