Imagine a scenario where you need to access a device located in a secure network from a remote location. The challenge? Ensuring that your connection remains safe and unbreachable while maintaining seamless control. This is where the concept of a remote control device behind firewall comes into play. In today’s interconnected world, businesses and individuals alike require robust solutions to manage devices remotely without compromising on security. Whether it’s controlling industrial machinery, managing home automation systems, or overseeing corporate servers, the ability to operate devices remotely has become indispensable. However, doing so securely requires a solid understanding of firewalls, network configurations, and encryption protocols.
Firewalls act as the first line of defense for any network, filtering out unauthorized access while allowing legitimate traffic to pass through. When you want to control a device remotely, ensuring that this communication happens securely behind a firewall is crucial. Modern technologies such as Virtual Private Networks (VPNs), Secure Shell (SSH) tunnels, and cloud-based solutions have made it easier than ever to achieve this balance between accessibility and security. This article will delve into the nuances of using a remote control device behind firewall, exploring best practices, potential risks, and practical implementation strategies. By the end, you’ll have a comprehensive guide to safeguarding your remote operations.
As we progress, we’ll also touch upon real-world examples and case studies to illustrate how organizations and individuals have successfully implemented these solutions. From small businesses to large enterprises, the demand for secure remote access continues to grow. This article aims to equip you with the knowledge and tools necessary to navigate this complex yet rewarding field. Whether you’re a tech enthusiast, an IT professional, or simply someone looking to enhance their cybersecurity posture, there’s something here for everyone. Let’s dive in!
Read also:Keanu Reeves Wife The Truth Behind His Love Life And Relationships
Table of Contents
- What Is a Remote Control Device?
- Why Use a Remote Control Device Behind Firewall?
- How Does a Firewall Enhance Security?
- Is It Safe to Access Devices Remotely?
- Best Practices for Secure Remote Access
- How to Set Up a Remote Control Device Behind Firewall?
- Common Mistakes to Avoid
- Case Studies and Real-World Examples
- Frequently Asked Questions
- Conclusion
What Is a Remote Control Device?
A remote control device refers to any hardware or software solution that enables users to interact with and manage devices from a distant location. These devices can range from simple household appliances like smart thermostats to complex industrial systems such as robotic arms in manufacturing plants. The key feature of a remote control device is its ability to function independently of physical proximity, making it an invaluable asset in modern-day applications.
Remote control devices are often paired with software platforms that facilitate communication between the user and the target device. For instance, you might use a smartphone app to adjust the temperature of your smart thermostat while away on vacation. Similarly, an IT administrator could troubleshoot a server issue using a remote desktop application. Regardless of the specific application, the underlying principle remains the same: enabling control over a device without being physically present.
However, the increasing reliance on remote control devices has also raised concerns about security. As these devices become more integrated into our daily lives, ensuring their protection against cyber threats becomes paramount. This is where the concept of deploying a remote control device behind firewall comes into play, offering a layer of security that helps mitigate potential risks.
Key Features of Remote Control Devices
- Ability to operate devices from a distance
- Support for various communication protocols
- Integration with cloud-based platforms
- Customizable settings for enhanced functionality
Why Use a Remote Control Device Behind Firewall?
Deploying a remote control device behind firewall offers several advantages, primarily centered around security and operational efficiency. Firewalls serve as gatekeepers, monitoring incoming and outgoing traffic to ensure only authorized connections are established. By placing a remote control device behind a firewall, you effectively shield it from unauthorized access attempts, reducing the risk of data breaches and other malicious activities.
One of the primary reasons for using a remote control device behind firewall is to protect sensitive information. For example, in a corporate environment, servers storing confidential customer data must be safeguarded against unauthorized access. A firewall ensures that only trusted users with the correct credentials can interact with these servers remotely. Additionally, firewalls can be configured to log all connection attempts, providing valuable insights into potential security threats.
Another benefit of using a remote control device behind firewall is improved network performance. By filtering out unnecessary traffic, firewalls help optimize bandwidth usage, ensuring that critical operations are not disrupted by extraneous data flows. This is particularly important in environments where multiple devices are connected to the same network, such as in a smart home or office setting.
Read also:Ofilmywap A Comprehensive Guide To The Popular Movie Streaming Platform
Benefits of Using a Firewall
- Enhanced security through access control
- Protection against unauthorized access
- Improved network performance
- Comprehensive logging and monitoring capabilities
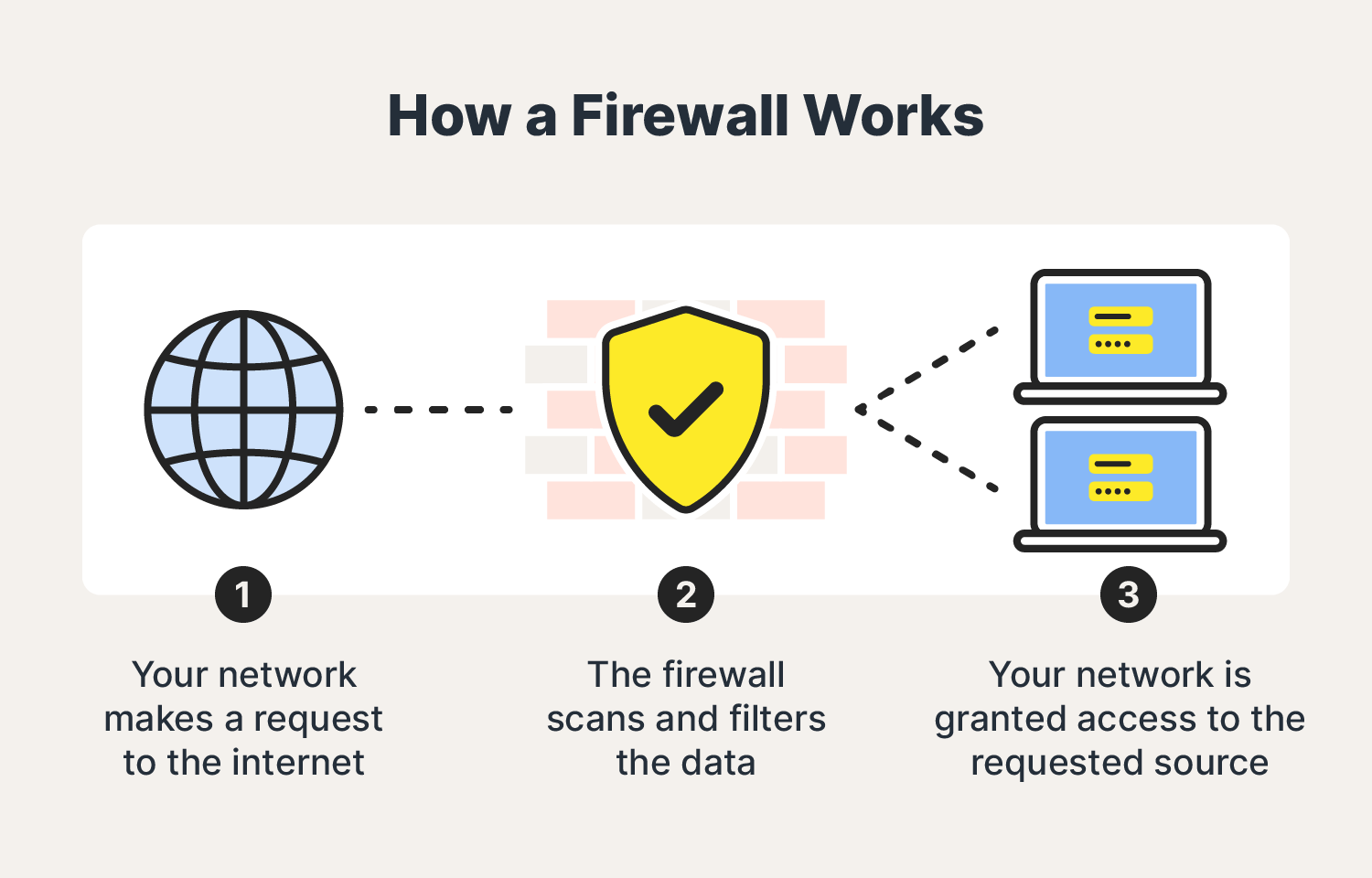
How Does a Firewall Enhance Security?
A firewall enhances security by acting as a barrier between your internal network and the external world. It examines each packet of data passing through the network, applying predefined rules to determine whether the traffic should be allowed or blocked. This process, known as packet filtering, ensures that only legitimate connections are established, significantly reducing the risk of cyberattacks.
In addition to packet filtering, modern firewalls offer advanced features such as intrusion detection and prevention systems (IDPS). These systems monitor network traffic for suspicious patterns and automatically block any activity that matches known attack signatures. Furthermore, firewalls can be configured to enforce strict access controls, requiring users to authenticate themselves before gaining access to protected resources.
For remote control devices, firewalls provide an additional layer of protection by encrypting communication channels. This ensures that even if an attacker intercepts the data being transmitted, they won’t be able to decipher its contents without the encryption key. As a result, deploying a remote control device behind firewall not only enhances security but also instills confidence in users that their operations are protected.
Types of Firewalls
- Packet Filtering Firewalls
- Stateful Inspection Firewalls
- Application-Level Gateways
- Next-Generation Firewalls
Is It Safe to Access Devices Remotely?
This is a question many people ask when considering the use of remote control devices. The short answer is yes, but only if proper security measures are in place. Accessing devices remotely inherently carries some risks, as it involves exposing your network to the internet. However, by implementing best practices and leveraging technologies like firewalls and encryption, you can significantly reduce these risks.
One of the most effective ways to ensure safe remote access is by using a Virtual Private Network (VPN). A VPN creates an encrypted tunnel between your device and the target network, shielding your communication from prying eyes. Additionally, employing strong authentication mechanisms, such as multi-factor authentication (MFA), adds another layer of protection, ensuring that only authorized users can access the system.
Regularly updating your software and firmware is another crucial step in maintaining secure remote access. Manufacturers frequently release patches and updates to address vulnerabilities, so staying current with these releases is essential. By combining these strategies, you can enjoy the convenience of remote access without compromising on security.
Common Security Risks in Remote Access
- Unsecured network connections
- Weak authentication mechanisms
- Outdated software and firmware
- Malicious insider threats
Best Practices for Secure Remote Access
Implementing best practices is essential for ensuring the security of remote control devices. Start by conducting a thorough risk assessment to identify potential vulnerabilities in your network. This will help you prioritize areas that require immediate attention and allocate resources effectively. Once you’ve identified the risks, follow these best practices to fortify your remote access setup:
First, always use a firewall to protect your network. Configure it to allow only necessary traffic and regularly review its rules to ensure they remain relevant. Next, employ encryption protocols such as SSL/TLS to secure communication channels. This prevents eavesdropping and ensures the integrity of your data. Additionally, enforce strong password policies and enable multi-factor authentication wherever possible.
Finally, educate your users about the importance of cybersecurity. Many breaches occur due to human error, so training employees and family members to recognize phishing attempts and other scams can go a long way in preventing incidents. By fostering a culture of security awareness, you create a more resilient network capable of withstanding various threats.
Steps to Enhance Security
- Conduct a risk assessment
- Implement a firewall
- Use encryption protocols
- Enforce strong authentication
- Provide cybersecurity training
How to Set Up a Remote Control Device Behind Firewall?
Setting up a remote control device behind firewall involves several steps, each requiring careful planning and execution. Begin by identifying the specific requirements of your application. For example, do you need to control a single device or multiple devices? Will the device be accessed from a fixed location or various locations? Answering these questions will help you determine the appropriate configuration for your setup.
Once you’ve clarified your needs, choose the right firewall solution for your environment. Options range from hardware-based firewalls to cloud-based services, each offering unique advantages depending on your use case. Next, configure the firewall to allow traffic only on the ports required by your remote control device. This minimizes the attack surface and reduces the likelihood of unauthorized access.
Finally, test your setup thoroughly to ensure everything functions as expected. Simulate different scenarios, including power outages and network failures, to verify the resilience of your configuration. Document your findings and refine your setup as needed. By following these steps, you can successfully deploy a remote control device behind firewall, enjoying both convenience and security.
Tips for Successful Deployment
- Plan your setup carefully
- Select the right firewall solution
- Configure ports and rules appropriately
- Test and refine your configuration
Common Mistakes to Avoid
While setting up a remote control device behind firewall, it’s easy to fall into common pitfalls that can compromise your security. One frequent mistake is neglecting to update your firewall firmware. Manufacturers regularly release updates to address newly discovered vulnerabilities, so failing to apply these updates leaves your network exposed.
Another common error is using default passwords and settings. Many devices come with preconfigured credentials that are widely known, making them easy targets for attackers. Always change these defaults immediately upon installation and use strong, unique passwords for all accounts. Similarly, avoid disabling security features like firewalls or encryption, as doing so undermines the very purpose of securing your network.
Lastly, don’t underestimate the importance of user education. Even the most secure system can be compromised by careless behavior, such as clicking on phishing links or sharing passwords. By educating your users about best practices and potential threats, you create a more secure environment for everyone involved.
Mistakes to Watch Out For
- Not updating firewall firmware
- Using default passwords
- Disabling security features
- Ignoring user education
Case Studies and Real-World Examples
Several organizations have successfully implemented remote control devices behind firewalls, achieving impressive results. One notable example is a manufacturing company that deployed industrial robots controlled remotely via a secure network. By leveraging advanced firewalls and encryption technologies, they ensured that production processes remained uninterrupted even during unexpected events like natural disasters.
In the healthcare sector, hospitals have embraced telemedicine solutions that rely on secure remote access. Physicians can now consult with patients and review medical records from anywhere in the world, all while maintaining compliance with strict privacy regulations. These implementations highlight the versatility and effectiveness of deploying remote control devices behind firewalls.
On a smaller scale, smart home enthusiasts have also benefited from this technology. By configuring firewalls to